Phishing or Fishing?
Either way it is bad news for your Email and more!
There has been a dramatic increase in the emails that you are receiving that are not what they seem to be. In the past these "Phishing" attempts have been mostly harmless. Now they are taking on a more nefarious purpose!
DON'T be a victim of these criminals. In recent months we have witnessed these hackers taking over Office 365 mailboxes and sending out fake invoices to the customers of the victim. These invoices have fake websites for taking payment information and in many cases ask for wire transfers in the HUNDREDS OF THOUSANDS of dollars!
Email is an essential part or our everyday communications. It is also one of the most common methods that hackers use to attempt to gain access to sensitive information. More than 90% of data breaches start with a phishing attack. “Phishing” uses fraudulent email messages designed to impersonate a legitimate person or organization and trick the recipient into downloading harmful attachments or divulging sensitive information, such as passwords, bank account numbers, and Social Security numbers.
Phishing scams can have a number of different goals. They may attempt to:
- Target your cash and payment card data
- Gain control of your computer and local network resources
- Gain access to your University Computing Account and resources
Phishing scams typically attempt to take advantage of you by:
- Delivering file attachments that can infect your computer with harmful software
- Enticing you to click on links to Web sites that infect your computer with harmful software
- Tricking you into sharing your username and password so hackers can gain access to your network or other sites
You can identify a phishing scam by looking for email messages that:
- The “reply to” email address is different from the sent from address
- Create a sense of urgency
- Request sensitive data
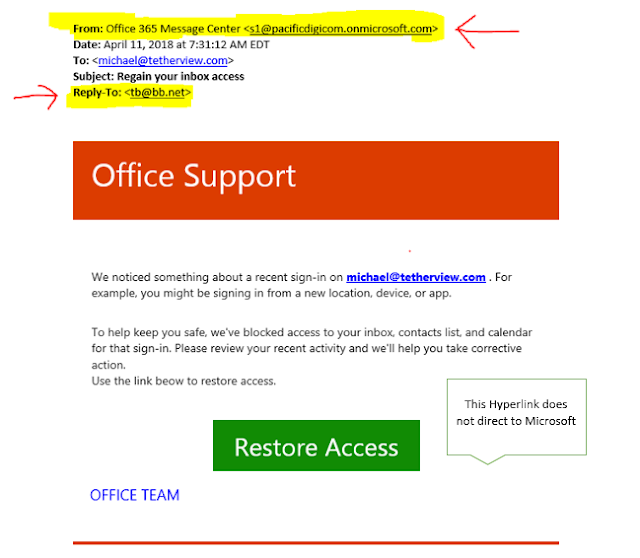
- Contain links that do not appear to match legitimate resources for the organization that is contacting you. Prior to clicking a link in ANY email verify the URL matches the anticipated site. See the example below
Phishing emails sometimes use Social Media to help coordinate the attack knowing that the person they are impersonating might be traveling or unavailable to respond to an urgent email. For example, attackers might follow someone on Facebook, when the target posts they are boarding a plane the attacker will send an email to their accounting team requesting an urgent payment to be sent.
Always remember that legitimate companies and organizations will never ask for passwords, social security numbers, and other sensitive data via email.
Here is an example of a Phishing Email!
These attacks are getting more prevalent and there are steps you can take to reduce the impact of when your team might be fooled into answering these FAKE emails.
We can assist in evaluating if you are susceptible to these attacks and make changes to your technical policies!
It is up to you to be aware of these requests and to NEVER click on the links and more important NEVER give out your email address and password unless it is to your IT provider.
Call us for a simple assessment and we can help save you from PHISHING like this!
Contact - info@tech-doctors.com 630-588-8325

Comments
Post a Comment